Using RemoteIoT behind a firewall on Windows can seem challenging, but with the right setup, it becomes manageable and secure. In today’s digital landscape, remote access tools like RemoteIoT are essential for managing IoT devices from anywhere. However, ensuring that these tools function seamlessly behind corporate or personal firewalls requires a solid understanding of networking principles and configuration steps.
Whether you're an IT professional, a network administrator, or someone who simply wants to connect to IoT devices securely, this guide will walk you through the process. We’ll explore the key concepts, tools, and techniques necessary to configure RemoteIoT behind a firewall on Windows systems. By the end of this article, you'll have a clear understanding of how to achieve secure and reliable remote access.
Our focus is on providing practical advice while adhering to best practices for network security. Let’s dive in and discover how to use RemoteIoT effectively, even when working within restrictive firewall environments.
Read also:Jon Hamm Net Worth 2024 A Comprehensive Look At The Actors Financial Empire
Table of Contents
- Introduction
- What is RemoteIoT?
- Understanding Firewalls
- Pre-Requisites for Using RemoteIoT
- Configuring Windows Firewall for RemoteIoT
- Port Forwarding and NAT
- Using a VPN for Secure Connections
- Troubleshooting Common Issues
- Best Practices for Secure RemoteIoT Access
- Conclusion
What is RemoteIoT?
RemoteIoT is a powerful tool designed to facilitate remote access to IoT devices. It allows users to monitor, control, and manage IoT devices from anywhere, making it an indispensable solution for modern businesses and individuals alike. The platform supports various protocols and offers robust security features, ensuring that your data remains protected during transmission.
Some key features of RemoteIoT include:
- Secure data encryption
- Customizable access permissions
- Real-time monitoring capabilities
- Integration with popular IoT platforms
Understanding what RemoteIoT offers is crucial before attempting to configure it behind a firewall. Let’s now delve deeper into the concept of firewalls and how they affect remote access.
Understanding Firewalls
A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Firewalls act as a barrier between trusted internal networks and untrusted external networks, such as the internet. They play a critical role in protecting sensitive data and preventing unauthorized access.
There are several types of firewalls, including:
- Packet-filtering firewalls
- Stateful inspection firewalls
- Application-layer firewalls
When using RemoteIoT behind a firewall, it’s essential to configure the firewall settings correctly to allow the necessary traffic while maintaining security. This involves understanding which ports and protocols RemoteIoT uses and adjusting firewall rules accordingly.
Read also:Iot Platform Remote Ssh Free The Ultimate Guide To Secure Connectivity
Why Firewalls Are Important
Firewalls help protect your network from malicious attacks, unauthorized access, and data breaches. By filtering out unwanted traffic, firewalls ensure that only legitimate connections are allowed to pass through. This is particularly important when working with IoT devices, which can be vulnerable to cyber threats.
Pre-Requisites for Using RemoteIoT
Before configuring RemoteIoT behind a firewall on Windows, there are a few pre-requisites you need to meet:
- A Windows computer with administrative privileges
- RemoteIoT software installed and configured
- Access to the firewall settings (either locally or through a network administrator)
- A basic understanding of networking concepts, such as IP addresses, ports, and protocols
Having these pre-requisites in place will make the configuration process smoother and more efficient. Let’s now explore how to configure the Windows firewall for RemoteIoT.
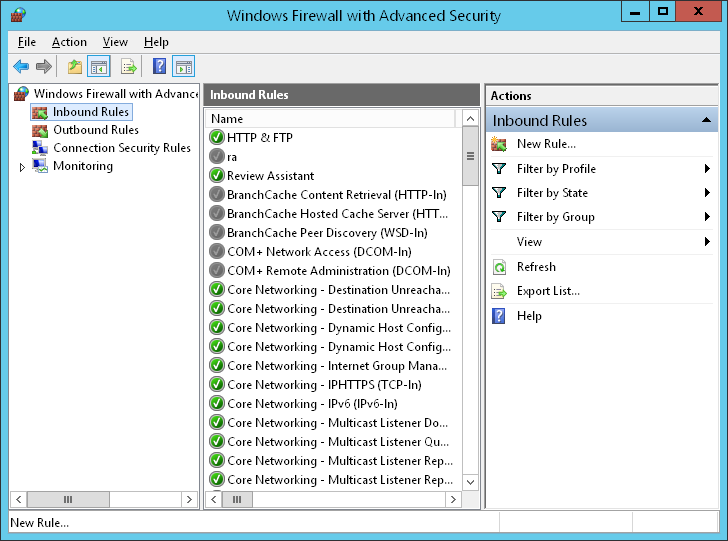
Configuring Windows Firewall for RemoteIoT
Windows Firewall is a built-in feature of Windows that provides basic network security. To use RemoteIoT behind a Windows firewall, you’ll need to create inbound and outbound rules that allow the necessary traffic.
Steps to Configure Windows Firewall
Follow these steps to configure Windows Firewall for RemoteIoT:
- Open the Windows Firewall settings by searching for "Windows Defender Firewall" in the Start menu.
- Click on "Advanced Settings" in the left-hand menu.
- In the Windows Defender Firewall with Advanced Security window, click on "Inbound Rules" in the left-hand menu.
- Click on "New Rule" in the right-hand menu and select "Port" as the rule type.
- Specify the port numbers used by RemoteIoT (e.g., TCP 8080) and choose "Allow the connection."
- Repeat the process for outbound rules if necessary.
By creating these rules, you ensure that RemoteIoT can communicate with your IoT devices without being blocked by the firewall.
Port Forwarding and NAT
Port forwarding is a technique used to allow external devices to connect to internal devices behind a firewall. It involves mapping specific ports on the firewall to internal IP addresses and ports. This is particularly useful when using RemoteIoT to access IoT devices from outside the local network.
How to Set Up Port Forwarding
To set up port forwarding for RemoteIoT, follow these steps:
- Log in to your router’s admin interface.
- Locate the "Port Forwarding" or "Virtual Servers" section.
- Create a new rule by specifying the external port, internal IP address, and internal port used by RemoteIoT.
- Save the changes and restart the router if necessary.
Network Address Translation (NAT) is another important concept to understand when working with firewalls and remote access. NAT allows multiple devices on a local network to share a single public IP address, making it easier to manage connections.
Using a VPN for Secure Connections
A Virtual Private Network (VPN) is an excellent option for securing remote connections to IoT devices. By creating an encrypted tunnel between your device and the network, a VPN ensures that all data transmitted is protected from prying eyes.
Some popular VPN solutions for RemoteIoT include:
- OpenVPN
- WireGuard
- IPsec
Using a VPN can simplify the process of configuring RemoteIoT behind a firewall, as it eliminates the need for complex port forwarding and firewall rules. However, it’s important to choose a reputable VPN provider and configure it properly to ensure maximum security.
Troubleshooting Common Issues
Even with careful configuration, issues can arise when using RemoteIoT behind a firewall. Here are some common problems and their solutions:
- Connection timeouts: Check that the necessary ports are open and that the firewall rules are correctly configured.
- Authentication errors: Verify that the credentials used for RemoteIoT are correct and that the device is authorized to access the network.
- Performance issues: Ensure that the network bandwidth is sufficient and that there are no bottlenecks in the connection.
If you encounter any of these issues, consult the RemoteIoT documentation or seek assistance from your network administrator.
Best Practices for Secure RemoteIoT Access
To ensure secure and reliable remote access to IoT devices, follow these best practices:
- Use strong passwords and enable two-factor authentication wherever possible.
- Regularly update RemoteIoT software and firmware to protect against vulnerabilities.
- Monitor network activity for any suspicious behavior and take action if necessary.
- Limit access to RemoteIoT to trusted users and devices only.
By adhering to these best practices, you can minimize the risk of security breaches and ensure that your IoT devices remain safe and accessible.
Conclusion
In conclusion, using RemoteIoT behind a firewall on Windows is a manageable task with the right configuration and setup. By understanding the principles of firewalls, port forwarding, and VPNs, you can ensure secure and reliable remote access to your IoT devices. This guide has provided you with the knowledge and tools necessary to configure RemoteIoT effectively, even in restrictive network environments.
We encourage you to share your experiences and tips in the comments section below. Additionally, feel free to explore other articles on our site for more insights into networking and IoT solutions. Together, let’s build a safer and more connected digital world.